Kubecost now available on Red Hat OpenShift OperatorHub
Kubecost is now available on Red Hat OpenShift OperatorHub. You can deploy Kubecost on your Red Hat OpenShift cluster in a more native way with just a few clicks.
Overview
Kubecost enables you to have granular visibility into your Kubernetes (K8s) application, starting at the K8s cluster level and going down to the containers level. Kubecost supports all K8s clusters or platforms running on different environments like public cloud, private cloud, or on-premises, including Red Hat OpenShift. You can learn more about the Kubecost installation on Red Hat OpenShift in this previous blog post. Today, we are excited to announce the availability of Kubecost’s operator on Red Hat OpenShift OperatorHub to help you deploy Kubecost on Red Hat Openshift cluster natively and easier.
Operator concept was introduced in 2016 by the CoreOS Linux development team. The operator manages software resources and their components as a software extension. With this launch, you can discover, try and deploy Kubecost’s operator from your Red Hat OpenShift OperatorHub web console with just a few clicks. Then, you can define your Kubecost deployment using Custom Resources Definition (CRD), apply it, and let Kubecost’s operator deploy and manage the lifecycle of Kubecost running inside your Red Hat Openshift cluster.
Discover Kubecost operator
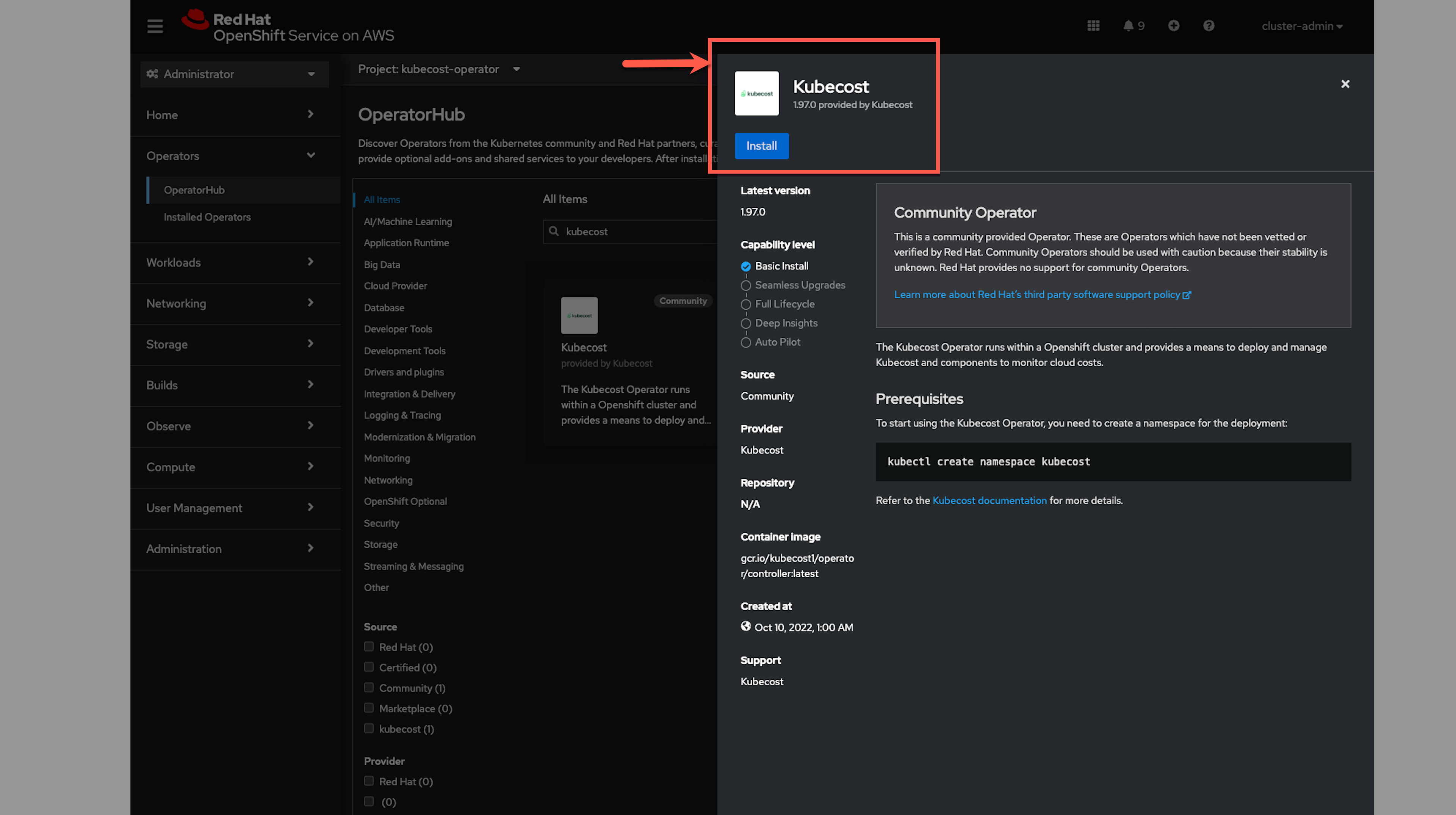
To find Kubecost Operator, you must log in to your Red Hat OpenShift cluster web console as an administrator. Next, on the left panel, navigate to Operators > OperatorHub, then type “Kubecost” in the search bar. Kubecost operator will be listed in the search result as in the following example screenshot:
Deploy Kubecost with Kubecost operator
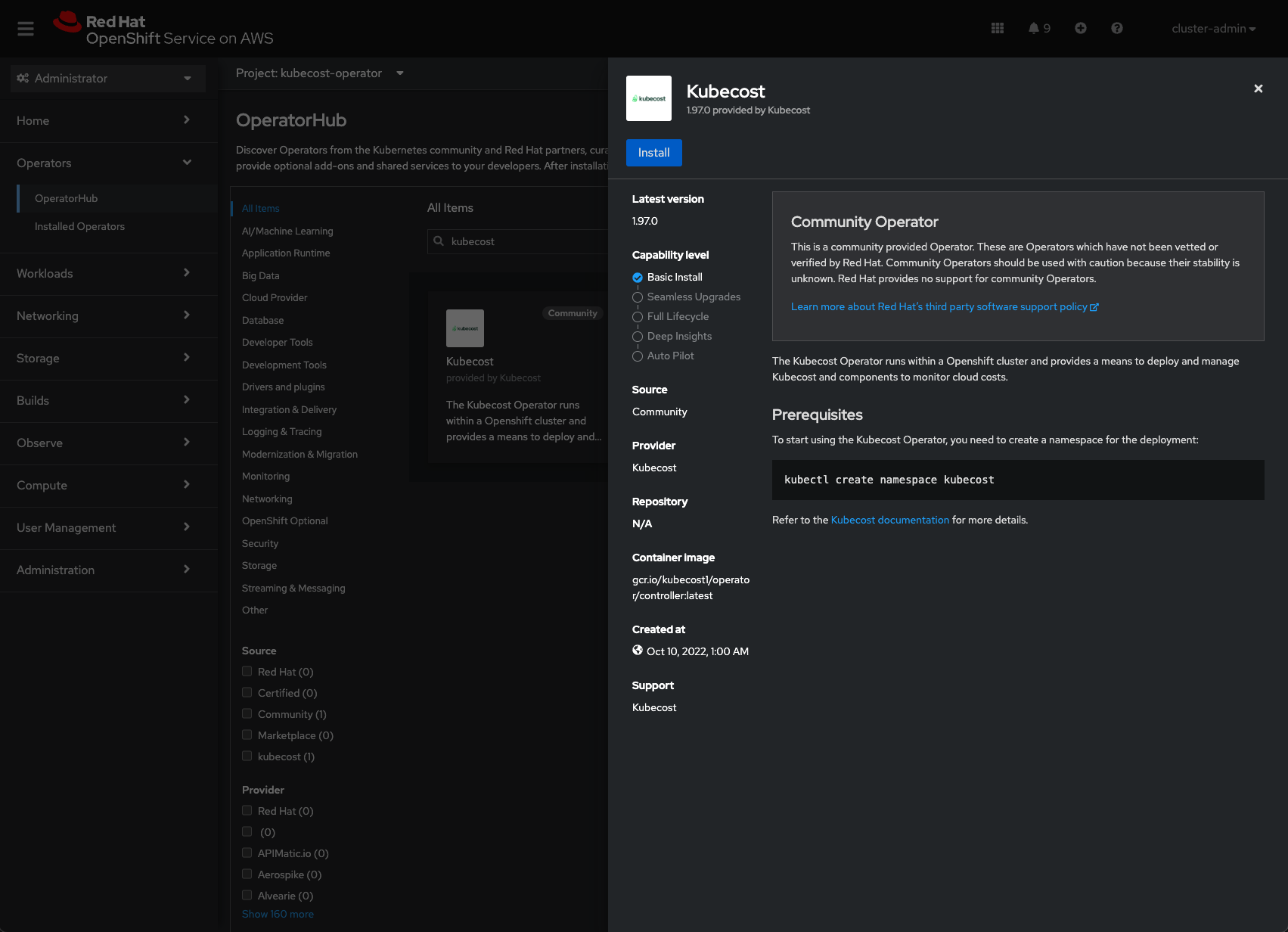
To install the Kubecost operator, you can click on the “Install” button and follow the on-screen instruction with default options. I take less than 2 minutes to install the Kubecost operator. The following example screenshot shows a successful installation of the Kubecost operator:
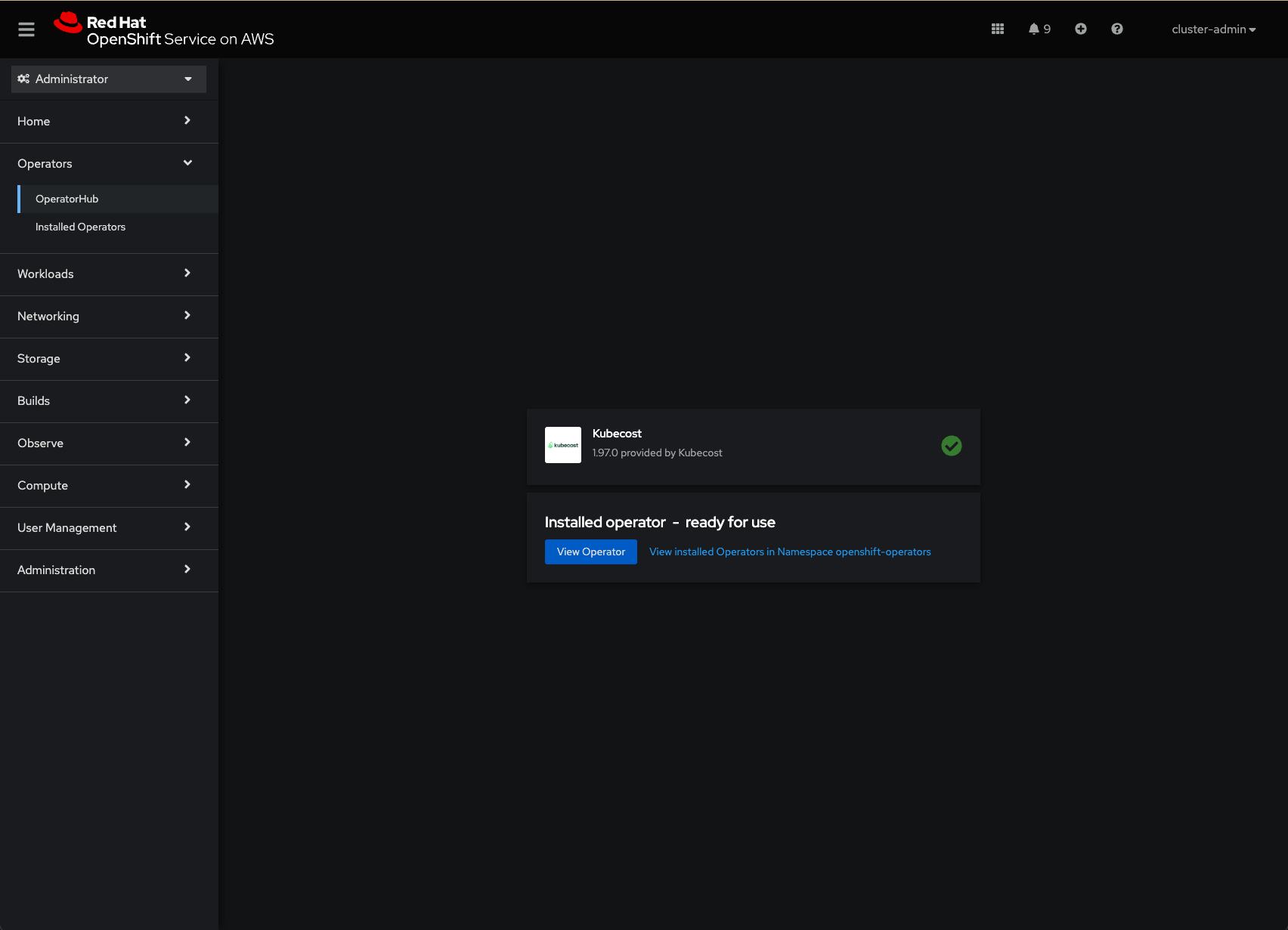
Once the Kubecost operator is up and running, you can start defining the custom resources definition to allow the Kubecost operator deploys and manages the Kubecost application. You can deploy Kubecost on Red Hat OpenShift cluster in the standard way using the following script:
cat << EOF > kubecost-crd.yaml
apiVersion: charts.kubecost.com/v1alpha1
kind: CostAnalyzer
metadata:
name: kubecost
spec:
affinity: {}
# Security Context settings for Redhat OpenShift cluster:
kubecostProductConfigs:
clusterName: YOUR_CLUSTER_NAME
# cloudIntegrationSecret: cloud-integration
kubecostDeployment:
podSecurityContext:
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
runAsNonRoot: true
kubecostModel:
etlCloudAsset: true # set to true to enable kubecost to include out-of-cluster cloud resources (uses more memory)
containerStatsEnabled: true
containerSecurityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
kubecostFrontend:
containerSecurityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
kubecostNetworkCosts:
securityContext: {}
containerSecurityContext: {}
prometheus:
nodeExporter:
enabled: false
kubeStateMetrics:
enabled: false
kube-state-metrics:
disabled: true
podSecurityPolicy:
enabled: false
server:
global:
external_labels:
cluster_id: YOUR_CLUSTER_NAME
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
sidecarContainers:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
configmapReload:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
grafana:
rbac:
pspEnabled: false
grafana:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
initContainers:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
sidecar:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
thanos:
thanosstore:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
thanosqueryfrontend:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
thanosquery:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
thanoscompact:
containerSecurityContext:
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
# Note: Un-comment these securityContext configs for OCP cluster 4.11+
# seccompProfile:
# type: RuntimeDefault
capabilities:
drop:
- ALL
# Disable Pod Security Policy (PSP)
# Kubecost PSP
podSecurityPolicy:
enabled: false
# Network Costs PSP
networkCosts:
enabled: false # if enabling network costs, also set the given cloud provider to true
config:
services:
amazon-web-services: false
google-cloud-services: false
azure-cloud-services: false
podSecurityPolicy:
enabled: false
# optional
global:
grafana:
enabled: false
proxy: false
EOF
kubectl create ns kubecost
kubectl apply -f kubecost-crd.yaml -n kubecost
You can find more detailed instructions in our documentation here.
Clean up
You can run the following command to uninstall Kubecost:
kubectl delete -f kubecost-crd.yaml -n kubecost
To uninstall the Kubecost operator, check this documentation.
Conclusion
In this blog, you have learned how to deploy Kubecost quickly with the Kubecost operator with just a few clicks. You can also check our documentation to learn about how to deploy Kubecost on Red Hat Openshift cluster using Helm Chart, or you can contact us in the following ways if you have questions or feedback.
We’re here to help!
Get in touch with a Kubecost team member to learn more about Kubecost Enterprise or request a custom demonstration.
Join us on Slack if you have questions or feedback, need help, or for general Kubernetes and cloud cost optimization conversation!